A computer virus, just like a virus we can contract, is annoying, stressful, bothersome, and reduces productivity. We try to avoid them but the cards aren’t always in our favor. Today’s fast-moving society makes it imperative that our electronic devices function properly. But, what happens when things begin to seem out-of-whack? Increased delays, strange messages, and unexpected application crashes could signify a problem. We fear the dreaded moment of realizing that our once trustworthy computer, has been suddenly attacked—but are we truly aware of the immense damage these viruses can have on us and our business?
A computer virus, just like a virus we can contract, is annoying, stressful, bothersome, and reduces productivity. We try to avoid them but the cards aren’t always in our favor. Today’s fast-moving society makes it imperative that our electronic devices function properly. But, what happens when things begin to seem out-of-whack? Increased delays, strange messages, and unexpected application crashes could signify a problem. We fear the dreaded moment of realizing that our once trustworthy computer, has been suddenly attacked—but are we truly aware of the immense damage these viruses can have on us and our business?
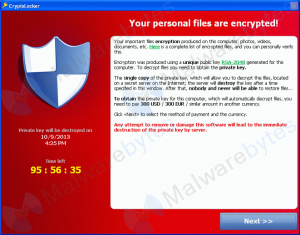
1. Ransomware
Beware! The use of ransomware has arrived and it’s taking computers by storm. Belgian, CryptoLocker and FBI MoneyPak, are the frontrunners in the ransomware war. They are independent of each other, but they share a common objective. Ransomware can spread through spam emails and hacked web pages. They will lock your computer, receive remote access, and command you to pay them ransom in order for your computer to be unlocked. If you do as the cybercriminals wish, will they really surrender their hold? We’re not entirely sure.
Belgian, specifically, requests you pay them $300 in 100 hours. If you do not meet their demand, they will wipe your entire computer. Scary! Check out our previous blog on CryptoLocker to learn more.
2. Trojans
Trojan advancements have skyrocketed this year, with Neverquest and Android trojans taking the lead. Neverquest is a banking trojan that’s spread via social media and email accounts. It has the ability to recognize hundreds of banking and financial websites and will obtain the user’s credentials upon logging in. It sends the information to its command center, which stores the information and uses it to drain money out of the victim’s account.
Unfortunately, trojans don’t stop with computers. Android trojans have infected millions of cellular devices this year. These trojans are capable of sending and deleting SMS messages, acquiring banking information, and downloading other malware. Worst yet—often times it cannot be detected and thus, cannot be removed!
3. Worms
Nidma and MyDoom have played significant roles in the history of malware. Nidma began in 2001, just following 9/11. It was spread via email, websites, and server vulnerabilities and became the most widespread worm in only 22 minutes. Due to its close timing to 9/11, some people speculated that it was implemented by Al-Qaeda. No evidence has proven this assumption to be true.
MyDoom was first sighted in 2004 and also spread like wildfire via email. When opened, MyDoom was able to record everything being typed (credit card information, passwords, etc…) by the usage of a “keystroke” program.
 4. “Ratters”
4. “Ratters”
“Ratters” are people who have maneuvered their ways through computer systems by using Remote Access Tools (RATs) to spy on their victims through webcams. It’s a complete invasion of privacy, as the victim is unaware and never gave consent. Could somebody be watching you right now? It’s hard to know. When you’re not using your camera, it’s wise to cover the lens. When your computer is not in use, be sure to shut it down.
5. Data & Security Breaches
Recently, Target has been a victim of the largest data and security breach in history. Although this attack didn’t affect our personal devices, it’s an extremely eye-opening situation for all businesspeople to learn from. Somehow, Target’s payment system was infected with malicious software, which allowed the cybercriminal(s) to steal money from 40 million people. It’s crucial to make sure your computer systems are properly protected, no matter how large or small your company may be. A small glitch in your system’s protection could lead to incredible repercussions.
Don’t fall victim to today’s technologically advanced and discreet computer viruses. Without proper prevention and maintenance, you may find yourself overwhelmed with the consequences that will undoubtedly follow. Take a look at our blog, 6 Ways to Protect Yourself From Viruses, to learn how to keep your computer—and your business—safe.
If you have a virus and need help now, please call 612-865-4475 or schedule an appt here.